Why Vulnerability Scanning Alone Isn’t Enough for API Security

In May 2021, the fitness company Peloton realized they had a problem with their APIs. The company, known for their fitness bikes, relied upon APIs to log members in and track their progress. The APIs also had access to account details such as name, address, and other personal information.
Then, a consultant for Pen Test Partners, Jan Masters, discovered a vulnerability that could make unauthorized requests to back-end APIs used by Peloton. Suddenly, all of the account information was available to anyone who knew where to look.
How could this happen? Companies today depend on APIs as a means of providing lightweight data streams to mobile applications, for example. They are used internally to share information between servers. Having a leak in either of these could potentially be devastating.
What is API Vulnerability Scanning?
Scanning is just another term for pattern matching. It’s taking the signature of a known vulnerability or misconfiguration and then parsing it within your code. While this ensures that your code is free from known vulnerabilities, it doesn’t identify any of the unknown vulnerabilities. It doesn’t find the zero days.
If you’re only looking for API compliance—a check box answer to “Is my API secure?”—then vulnerability scanning can provide that. It doesn’t, however, mean that your API is truly secure. It doesn’t rule out the potential for your APIs to be leaking sensitive information.
Taking Your API Security to the Next Level With Active Testing
In addition to testing the performance and reliability of your API—which you are most likely already doing—wouldn’t you also like to know that the API is actually secure?
Going beyond scanning your API means actually testing the API. Fuzz testing is an excellent method for API testing. Fuzz testing creates random inputs to help discover areas where your API may have the potential for data leakage or, at the very least, weak performance. Additionally, fuzzing can expose Common Weakness Enumerations (CWEs), so your developers know where and how to fix the problems.
Mayhem: An API Testing Solution That Goes Beyond Vulnerability Scanning
Mayhem is an API testing solution that combines fuzz testing with other active API testing methods. Mayhem was built from the ground up to test the performance, reliability, and security of your APIs. No need to recompile, no need to configure. Just point Mayhem at your API and start testing within five minutes.
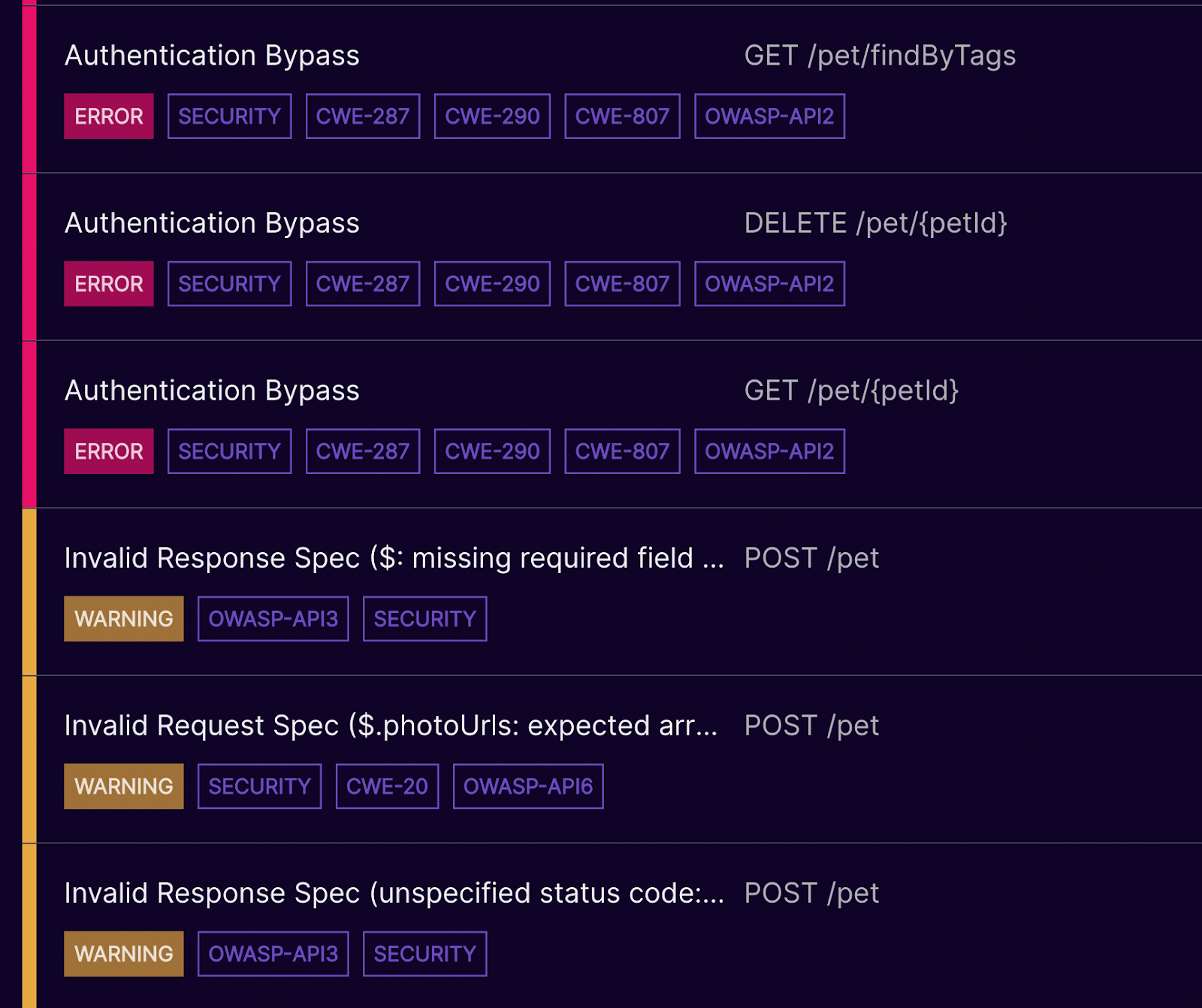
Looking to comply with the OWASP API Top 10? No problem. Mayhem uses Zed Attack Proxy (ZAP). Unlike running ZAP by itself, Mayhem triages the results so that you see the most critical first. And Mayhem performs additional tests not included in ZAP.
Why put a band-aid on it when you can address and heal the problems at their source? Sign up today for a free version of Mayhem for API.
Complete API Security in 5 Minutes
Get started with Mayhem today for fast, comprehensive, API security.
Get Mayhem for API Free
Add Mayhem to Your DevSecOps for Free.
Get a full-featured 30 day free trial.




.jpg)