How to Run Mayhem from a Docker Image

Provided as an easy-to-use web interface and fuzzing platform, users can use the Mayhem UI to create, manage, and analyze their Mayhem fuzzing runs on containerized applications, or targets, residing within Docker images that have been uploaded to the public Docker Hub registry.
How do you do this? It's as easy as:
- Logging in to the Mayhem UI hosted on your Mayhem deployment.
- Selecting a Docker Image for your new Mayhem run.
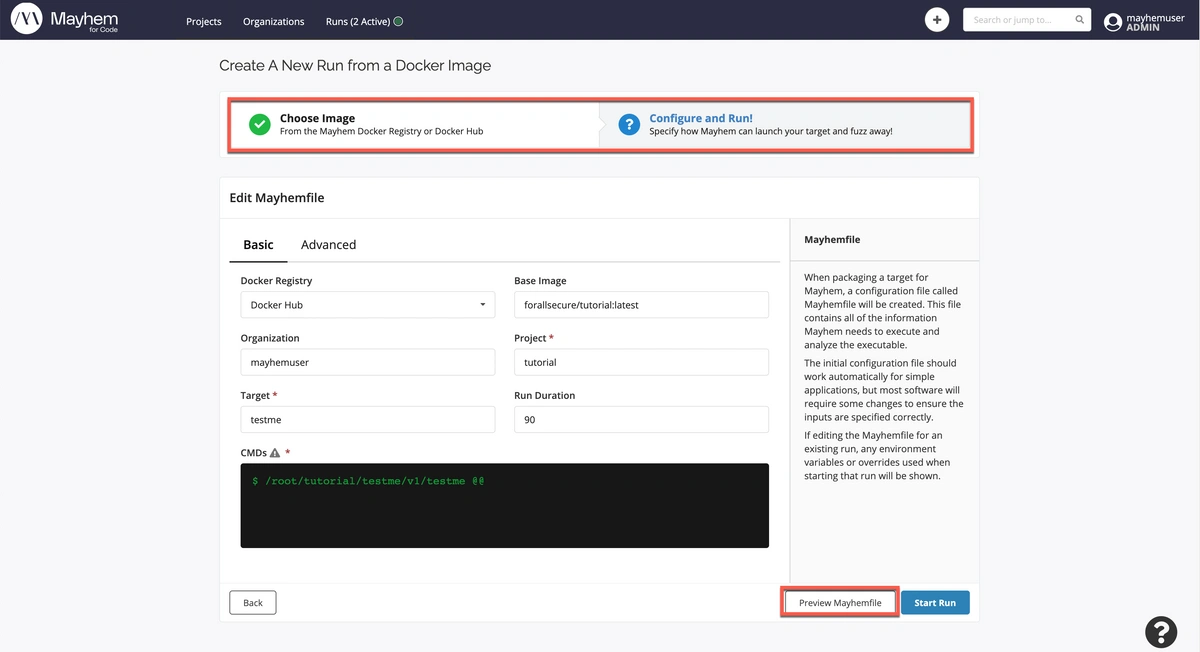
- Configuring the Mayhemfile for the run.
- Executing your new Mayhem run!
Let's see how this works in more detail. To get you quickly started, we've provided a button for you to create a new pre-configured run using a Docker image hosted on Docker Hub. For this exercise we will be executing a Mayhem run on the previously discussed testme
Then, simply click Next until you get to the end of the create new run flow and click Start Run to confirm your selections and execute your first Mayhem run!
After executing the Mayhem run, you should see the following run analysis page:

The run analysis page indicates the progress of the Mayhem run and will continue to auto-refresh until the end of its duration. In this time, Mayhem will fuzz the target application and generate as many test cases as it can to detect potential security vulnerabilities in the target application. Test cases that result in crashes or defects will be marked accordingly for future reference.
In particular, if we scroll down to the bottom of the run analysis page, we can see more information about what defects Mayhem found when fuzzing the containerized testme target and even the individual test cases that were used during fuzzing.
For this particulartestme target, there appears to be an underlying improper input validation defect.
Note. The exact hash/ID of your test case for your specific Mayhem run may differ from what is shown in this lesson.
Development Speed or Code Security. Why Not Both?
Mayhem is an award-winning AI that autonomously finds new exploitable bugs and improves your test suites.
Get Mayhem Free Request A Demo
And when we switch the pane's view from Defects to Test Cases, we see the individual breakdown of test cases generated during the Mayhem run; Mayhem generated two particular test cases for this run resulting in the specified defect.

Nice job executing your first Mayhem run and finding a defect for the testme target binary!
To confirm that the defect is indeed valid, we can reproduce the defective behavior of the testme binary by manually fuzzing the testme binary with the test case that Mayhem generated and saved. Users can download their test cases for this very use case.
Add Mayhem to Your DevSecOps for Free.
Get a full-featured 30 day free trial.




.jpg)